In today’s fast-paced IT landscape, the ability to respond quickly and effectively to security incidents is paramount. Gone are the days of manually triaging alerts and painstakingly implementing fixes. Businesses need agility and automation to stay ahead of threats, minimize downtime, and protect sensitive data. This is where the power of automated incident response, driven by advanced Remote Monitoring and Management (RMM) platforms, comes into play. It’s not just about monitoring; it’s about proactive intervention.
Think of an RMM as your IT team’s tireless assistant, constantly watching over your entire infrastructure, from servers and workstations to network devices and cloud services. But modern RMM solutions are far more than just passive observers. They’re equipped with sophisticated automation capabilities that enable them to detect, diagnose, and remediate incidents with minimal human intervention. This means your IT staff can focus on strategic initiatives and complex problem-solving, rather than getting bogged down in repetitive, time-consuming tasks.

This article will delve into the world of automated incident response through advanced RMM, exploring its key features, benefits, and practical implementation. We’ll examine how these platforms can empower your IT team to proactively address security threats, improve operational efficiency, and ultimately, deliver a more secure and reliable IT environment. Get ready to unlock the full potential of your RMM and transform your incident response strategy.
What is Automated Incident Response?
Automated incident response is the process of using technology to automatically detect, analyze, and remediate security incidents or IT issues without requiring manual intervention from IT personnel. It leverages pre-defined rules, workflows, and automation scripts within an RMM platform to quickly address common problems, freeing up IT staff to focus on more complex and strategic tasks. Effective IT management often necessitates tools like RMM to streamline operations and enhance security.
Key Components of Automated Incident Response
Several components work together to create an effective automated incident response system:
- Threat Detection: Identifying potential security threats or system anomalies through real-time monitoring and analysis of logs, events, and performance metrics.
- Incident Analysis: Automatically analyzing detected incidents to determine their severity, scope, and potential impact on the organization.
- Containment: Isolating affected systems or network segments to prevent the spread of the incident.
- Remediation: Implementing automated actions to resolve the incident, such as patching vulnerabilities, removing malware, or resetting passwords.
- Reporting and Documentation: Automatically generating reports on incident details, actions taken, and outcomes for auditing and compliance purposes.
The Role of Advanced RMM in Automated Incident Response
Advanced RMM platforms serve as the foundation for automated incident response. They provide the necessary infrastructure, monitoring capabilities, and automation tools to effectively detect, analyze, and remediate incidents.
Real-time Monitoring and Alerting
RMM platforms continuously monitor systems, networks, and applications for suspicious activity and performance anomalies. They generate alerts based on predefined thresholds and security policies, notifying IT staff of potential incidents in real-time. The key here is configurable alerting: you don’t want to be swamped with false positives, so fine-tuning is crucial.
Automation Capabilities
The automation engine within an RMM platform is the heart of automated incident response. It allows IT teams to define automated workflows and scripts that are triggered by specific events or alerts. These workflows can automate tasks such as:
- Restarting services
- Killing processes
- Running scripts to fix common issues
- Patching vulnerabilities
- Isolating infected machines
- Sending notifications to relevant personnel
Integration with Security Tools
Modern RMM platforms integrate with other security tools, such as antivirus software, firewalls, and intrusion detection systems, to provide a more comprehensive security posture. This integration allows the RMM to correlate data from multiple sources and automate responses based on a broader range of threat intelligence.
Benefits of Automated Incident Response
Implementing automated incident response through advanced RMM offers numerous benefits for organizations of all sizes.
Faster Response Times
Automation significantly reduces the time it takes to respond to security incidents. By automating repetitive tasks, IT staff can quickly contain and remediate threats, minimizing potential damage and downtime. Think about the difference between manually patching 100 machines versus triggering an automated patch deployment across your entire network. The time savings are substantial.
Reduced Downtime
By quickly resolving incidents, automated incident response helps to minimize downtime and maintain business continuity. This is particularly important for critical systems and applications that are essential for business operations.

Improved Security Posture
Automated incident response strengthens an organization’s overall security posture by proactively addressing vulnerabilities and responding to threats in a timely manner. This reduces the risk of data breaches, malware infections, and other security incidents.
Increased Efficiency
Automation frees up IT staff to focus on more strategic tasks and complex problem-solving. This improves overall efficiency and productivity, allowing IT teams to deliver more value to the business.
Reduced Costs
By automating incident response, organizations can reduce the costs associated with manual incident handling, such as overtime pay, consulting fees, and lost productivity. It also helps to avoid the potentially much larger costs associated with security breaches and data loss.
Challenges in Implementing Automated Incident Response
While the benefits of automated incident response are significant, there are also some challenges to consider when implementing these solutions.
Complexity of Configuration
Configuring automated workflows and scripts can be complex, requiring a deep understanding of the RMM platform and the specific security threats being addressed. Proper planning and testing are crucial to ensure that automation rules are effective and do not inadvertently disrupt business operations. You need to understand the “if this, then that” logic and how it applies to your specific environment.
False Positives
False positives can trigger unnecessary automated actions, potentially causing disruptions to business operations. It’s important to carefully tune monitoring thresholds and security policies to minimize false positives and ensure that alerts are accurate and reliable. Regular review and adjustment of these thresholds is a must.
Lack of Human Oversight
While automation is valuable, it’s important to maintain human oversight to ensure that automated actions are appropriate and effective. In some cases, human intervention may be necessary to handle complex or unusual incidents. The key is finding the right balance between automation and human control.
Integration Challenges
Integrating an RMM platform with other security tools can be challenging, requiring careful planning and configuration. It’s important to ensure that the integration is seamless and that data is shared effectively between the different systems.
Best Practices for Implementing Automated Incident Response
To ensure a successful implementation of automated incident response, consider the following best practices:
Start with a Clear Strategy
Define your goals and objectives for automated incident response. Identify the specific security threats and IT issues that you want to address, and develop a clear plan for implementing automation rules and workflows. This includes identifying key stakeholders and defining roles and responsibilities.
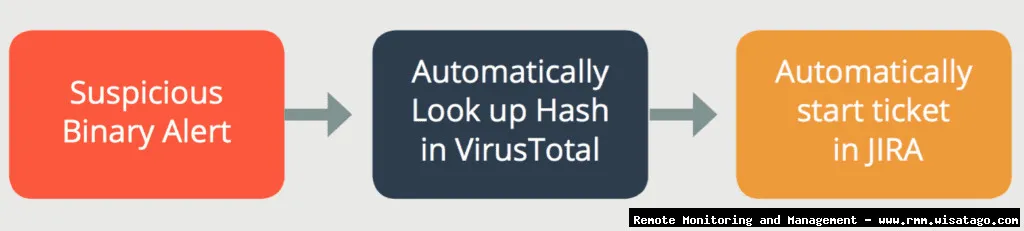
Prioritize Automation Efforts
Focus on automating the most common and repetitive tasks first. This will provide the greatest immediate benefit and allow you to gradually expand your automation efforts over time. Start with low-risk, high-impact tasks to build confidence and demonstrate the value of automation.
Thoroughly Test Automation Rules
Before deploying automation rules to a production environment, thoroughly test them in a staging environment to ensure that they function as expected and do not cause any unintended consequences. This testing should include a variety of scenarios to simulate real-world conditions.
Monitor and Refine Automation Rules
Continuously monitor the performance of automation rules and refine them as needed to improve their effectiveness and accuracy. Regularly review logs and reports to identify any issues or areas for improvement. This is an ongoing process, not a one-time setup.
Provide Training and Documentation
Provide adequate training to IT staff on how to use the RMM platform and manage automated incident response. Create comprehensive documentation to guide users through the configuration and maintenance of automation rules. Knowledge is power, and ensuring your team understands the system is critical.
Choosing the Right RMM Platform for Automated Incident Response
Selecting the right RMM platform is crucial for successful automated incident response. Consider the following factors when evaluating RMM solutions:
Automation Capabilities
Ensure that the RMM platform offers robust automation capabilities, including the ability to define custom workflows and scripts. Look for a platform that supports a wide range of automation actions and integrations with other security tools.
Monitoring and Alerting
Choose an RMM platform that provides comprehensive monitoring and alerting capabilities, with the ability to detect a wide range of security threats and IT issues. The platform should offer customizable alert thresholds and notifications to ensure that you are alerted to the most important events.
Integration with Security Tools
Select an RMM platform that integrates seamlessly with other security tools, such as antivirus software, firewalls, and intrusion detection systems. This integration will provide a more comprehensive security posture and enable more effective automated incident response.
Scalability and Reliability
Ensure that the RMM platform is scalable and reliable, capable of handling the demands of your organization’s IT infrastructure. The platform should be able to monitor a large number of devices and systems without performance degradation.
Ease of Use
Choose an RMM platform that is easy to use and manage. The platform should have a user-friendly interface and intuitive workflows to simplify the configuration and maintenance of automated incident response.

Conclusion
Automated incident response through advanced RMM is a powerful tool for improving an organization’s security posture, reducing downtime, and increasing IT efficiency. By automating repetitive tasks and proactively addressing security threats, IT teams can free up their time to focus on more strategic initiatives and deliver greater value to the business. While there are challenges to consider when implementing these solutions, following best practices and choosing the right RMM platform can help organizations achieve significant benefits. The future of IT security lies in proactive, automated defense, and advanced RMM is at the forefront of this revolution.
Conclusion
In conclusion, automated incident response through advanced RMM platforms represents a paradigm shift in IT management. By leveraging automation, businesses can significantly reduce response times, minimize downtime, and alleviate the burden on IT staff. The ability to proactively identify, diagnose, and resolve incidents without manual intervention translates to enhanced operational efficiency, improved security posture, and a more resilient IT infrastructure. Embracing this technology allows organizations to move beyond reactive firefighting and towards a proactive, strategic approach to IT incident management.
The integration of advanced RMM with automated incident response capabilities is no longer a luxury, but a necessity in today’s fast-paced and threat-laden digital landscape. To truly future-proof your IT operations and maximize the value of your technology investments, we encourage you to explore the potential of advanced RMM solutions. Discover how these platforms can empower your team, streamline your workflows, and ultimately, drive significant improvements in your organization’s overall performance. Learn more about how to implement these solutions by visiting our resources page.
Frequently Asked Questions (FAQ) about Automated Incident Response through Advanced RMM
How can automated incident response through an advanced RMM platform help me reduce IT downtime and improve overall business continuity?
Automated incident response capabilities within an advanced Remote Monitoring and Management (RMM) platform can significantly reduce IT downtime and bolster business continuity by enabling proactive detection and rapid remediation of issues. The RMM platform continuously monitors systems, networks, and applications, identifying anomalies and potential threats in real-time. When an incident is detected, predefined automated workflows are triggered. These workflows can include actions such as restarting services, isolating infected machines, running scripts to fix common problems, and alerting IT staff. By automating these tasks, the response time is dramatically reduced, minimizing the impact of incidents and preventing them from escalating into major outages. This proactive approach ensures business continuity by keeping critical systems operational and minimizing disruptions to workflows.
What specific types of IT security incidents can be automatically resolved or mitigated using an advanced RMM platform’s incident response features?
An advanced RMM platform with automated incident response can address a wide range of IT security incidents. Some common examples include malware detection and removal, where the RMM can automatically quarantine infected systems and initiate anti-malware scans. Patch management automation can address vulnerability exploits, by automatically deploying critical security patches to prevent breaches. The RMM can also mitigate unauthorized access attempts by disabling compromised accounts, blocking suspicious IP addresses, and enforcing multi-factor authentication. Furthermore, it can resolve issues stemming from resource exhaustion, such as high CPU or memory usage, by automatically restarting services or allocating additional resources. These automated responses enable rapid containment and remediation, reducing the potential damage from security incidents and minimizing the workload on IT staff.
What are the key benefits of integrating my existing security tools (like SIEM and endpoint detection) with an RMM platform for automated incident response, and how does this integration work?
Integrating existing security tools like SIEM (Security Information and Event Management) and endpoint detection and response (EDR) solutions with an RMM platform for automated incident response offers several key benefits. It creates a more holistic and proactive security posture by centralizing threat intelligence and automating response workflows. SIEM solutions provide comprehensive security event monitoring and correlation, while EDR tools focus on detecting and responding to threats at the endpoint level. By integrating these tools with an RMM, security alerts and threat intelligence from the SIEM and EDR can automatically trigger predefined actions within the RMM. This can include isolating infected endpoints, running remediation scripts, or escalating alerts to security analysts. The integration typically involves API connections that allow the RMM to receive and process security alerts from the other tools, enabling a coordinated and automated response to security incidents. This reduces manual intervention, improves response times, and enhances overall security effectiveness.