In today’s complex IT landscape, compliance isn’t just a nice-to-have; it’s a critical business imperative. Whether you’re dealing with HIPAA for healthcare, PCI DSS for financial transactions, GDPR for data privacy, or a myriad of other regulations, the pressure to maintain compliance is immense. Failure to comply can result in hefty fines, reputational damage, and even legal action. For many IT professionals, especially those managing multiple endpoints and clients, ensuring compliance can feel like an overwhelming task.
That’s where premium Remote Monitoring and Management (RMM) software comes into play. These sophisticated tools go beyond basic monitoring and patching; they offer robust compliance management features designed to streamline the entire process, from assessment to remediation and reporting. Think of it as having a dedicated compliance officer built into your IT management platform, constantly vigilant and proactively addressing potential risks. This article will delve into the specific compliance features you can expect from premium RMM solutions and how they can significantly ease the burden of maintaining regulatory adherence.

We’ll explore the core functionalities, such as automated policy enforcement, vulnerability scanning, audit trails, and reporting capabilities. We’ll also discuss the real-world benefits of using these features, including reduced risk, improved efficiency, and enhanced security posture. By the end of this guide, you’ll have a comprehensive understanding of how premium RMM software can be a game-changer for your compliance efforts, allowing you to focus on strategic IT initiatives rather than constantly fire-fighting compliance issues.
Compliance Management Features In Premium RMM Software: Complete Guide, Features and Details
Premium RMM solutions provide a comprehensive suite of features designed to simplify and automate the often-complex process of compliance management. These features help IT professionals proactively identify, address, and report on compliance-related issues, ultimately reducing risk and improving overall security posture.
Automated Policy Enforcement
One of the most valuable compliance features in premium RMM software is automated policy enforcement. This allows you to define and automatically apply security policies across all managed endpoints. For example, you can enforce password complexity requirements, screen lock timeouts, and application whitelisting/blacklisting. The RMM agent constantly monitors each endpoint to ensure compliance with these policies and automatically remediates any deviations.
Benefits:
- Consistent Security Posture: Ensures that all devices adhere to the same security standards, regardless of location or user.
- Reduced Risk: Minimizes the risk of human error and oversight in policy implementation.
- Improved Efficiency: Automates repetitive tasks, freeing up IT staff to focus on more strategic initiatives.
Example: Enforcing a policy that requires all computers to have disk encryption enabled. The RMM automatically checks for encryption status and encrypts drives that are not compliant.
Vulnerability Scanning and Management
Identifying and addressing vulnerabilities is crucial for maintaining compliance with many regulations. Premium RMM solutions integrate with vulnerability scanners to automatically detect security weaknesses in operating systems, applications, and network devices. These scanners can identify missing patches, outdated software versions, and misconfigurations that could be exploited by attackers.
Benefits:
- Proactive Risk Mitigation: Identifies and addresses vulnerabilities before they can be exploited.
- Reduced Attack Surface: Minimizes the number of potential entry points for attackers.
- Improved Compliance: Helps meet the vulnerability management requirements of various regulations.
Example: Scheduling regular vulnerability scans to identify systems vulnerable to the latest zero-day exploits. The RMM then automatically deploys necessary patches and updates to mitigate the risk.
Patch Management
Closely related to vulnerability scanning is patch management. Premium RMMs provide robust patch management capabilities, allowing you to automatically deploy software updates and security patches to all managed devices. This ensures that systems are protected against known vulnerabilities and that they meet the patching requirements of various compliance regulations.
Benefits:
- Automated Updates: Simplifies the process of keeping systems up-to-date with the latest security patches.
- Reduced Downtime: Allows for scheduled patching during off-peak hours to minimize disruption to users.
- Improved Security: Protects systems against known vulnerabilities and reduces the risk of successful attacks.
Example: Automatically deploying Windows updates and third-party application patches to all computers on a weekly basis, ensuring that systems are protected against known vulnerabilities.
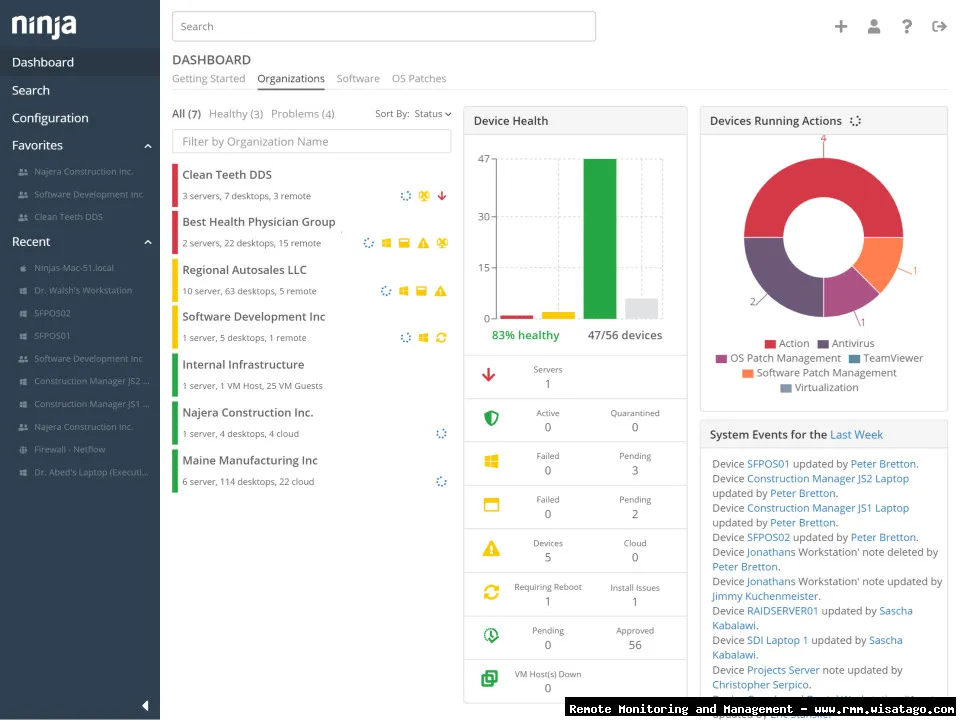
. Effective IT management often involves proactive monitoring, and RMM plays a crucial role in that process
.
Audit Trails and Logging
Detailed audit trails are essential for demonstrating compliance to auditors. Premium RMM solutions provide comprehensive logging capabilities, tracking all user activity, system changes, and security events. This information can be used to reconstruct past events, identify security breaches, and demonstrate adherence to compliance requirements.
Benefits:
- Improved Accountability: Provides a clear record of all user activity and system changes.
- Enhanced Security: Helps identify and investigate security incidents.
- Simplified Audits: Makes it easier to demonstrate compliance to auditors by providing a comprehensive audit trail.
Example: Logging all user logins and logouts, file access attempts, and system configuration changes. This information can be used to investigate potential security breaches and demonstrate compliance with data security regulations.
Reporting and Compliance Dashboards
Generating reports that demonstrate compliance can be a time-consuming and challenging task. Premium RMM solutions offer pre-built reports and customizable dashboards that provide a clear overview of your compliance status. These reports can be used to demonstrate adherence to specific regulations, such as HIPAA, PCI DSS, and GDPR.
Benefits:
- Simplified Reporting: Provides pre-built reports that demonstrate compliance with various regulations.
- Improved Visibility: Offers a clear overview of your compliance status through customizable dashboards.
- Reduced Audit Preparation Time: Makes it easier to prepare for audits by providing readily available compliance reports.
Example: Generating a report that shows the percentage of devices that are compliant with a specific security policy, such as password complexity requirements. This report can be used to demonstrate compliance with data security regulations.
Configuration Management
Maintaining consistent configurations across all devices is crucial for security and compliance. Premium RMMs allow you to define and enforce configuration baselines, ensuring that all systems are configured according to your security policies. This helps prevent misconfigurations that could lead to vulnerabilities or compliance violations.
Benefits:
- Consistent Configurations: Ensures that all devices are configured according to your security policies.
- Reduced Risk of Misconfiguration: Prevents misconfigurations that could lead to vulnerabilities or compliance violations.
- Improved Security Posture: Enhances overall security by enforcing consistent security settings across all devices.
Example: Enforcing a configuration baseline that requires all computers to have a specific firewall configuration. The RMM automatically checks for compliance and remediates any deviations.
Remote Access Control
Controlling remote access to systems is essential for security and compliance. Premium RMMs provide granular control over remote access permissions, allowing you to restrict access to authorized users only. This helps prevent unauthorized access to sensitive data and systems.
Benefits:

- Enhanced Security: Prevents unauthorized access to sensitive data and systems.
- Improved Compliance: Helps meet the remote access control requirements of various regulations.
- Reduced Risk of Data Breaches: Minimizes the risk of data breaches caused by unauthorized remote access.
Example: Requiring multi-factor authentication for all remote access connections and restricting access to specific IP addresses. This helps prevent unauthorized access to sensitive data and systems.
Integration with Security Information and Event Management (SIEM) Systems
Many premium RMM solutions integrate with SIEM systems, allowing you to centralize security event data from multiple sources. This provides a comprehensive view of your security posture and helps you identify and respond to security threats more effectively. Integration with SIEM systems is often required for compliance with certain regulations.
Benefits:
- Centralized Security Event Data: Provides a comprehensive view of your security posture.
- Improved Threat Detection: Helps you identify and respond to security threats more effectively.
- Enhanced Compliance: Simplifies the process of meeting the logging and monitoring requirements of various regulations.
Example: Forwarding security event logs from all managed devices to a SIEM system for analysis and correlation. This allows you to identify and respond to security threats more effectively.
Data Encryption Management
Protecting sensitive data at rest and in transit is a critical compliance requirement. Premium RMMs often include features for managing data encryption, ensuring that all sensitive data is encrypted and protected against unauthorized access.
Benefits:
- Enhanced Data Security: Protects sensitive data against unauthorized access.
- Improved Compliance: Helps meet the data encryption requirements of various regulations.
- Reduced Risk of Data Breaches: Minimizes the risk of data breaches caused by data theft or loss.
Example: Enforcing full disk encryption on all laptops and desktops, and requiring encryption for all data transmitted over the network. This helps protect sensitive data against unauthorized access.
Challenges and Considerations
While premium RMM software offers significant benefits for compliance management, there are also challenges and considerations to keep in mind:
- Complexity: RMM solutions can be complex to configure and manage, requiring specialized expertise.
- Cost: Premium RMM solutions can be expensive, especially for small businesses.
- Integration: Integrating RMM with existing IT systems can be challenging.
- Training: IT staff may require training to effectively use the RMM‘s compliance management features.
- Ongoing Maintenance: RMM solutions require ongoing maintenance and updates to ensure they remain effective.
Despite these challenges, the benefits of using premium RMM software for compliance management far outweigh the drawbacks. By carefully planning your implementation and investing in proper training, you can leverage the power of RMM to streamline your compliance efforts and reduce your risk of non-compliance.
Conclusion
Premium RMM software offers a powerful suite of compliance management features that can significantly simplify and automate the process of maintaining regulatory adherence. From automated policy enforcement to vulnerability scanning, audit trails, and reporting capabilities, these tools provide IT professionals with the resources they need to proactively identify, address, and report on compliance-related issues. While there are challenges associated with implementing and managing RMM solutions, the benefits of reduced risk, improved efficiency, and enhanced security posture make them a worthwhile investment for any organization that takes compliance seriously. By choosing the right RMM solution and investing in proper training, you can transform your compliance efforts from a reactive burden into a proactive strategic advantage.
Conclusion
In conclusion, the integration of robust compliance management features within premium RMM software represents a significant evolution in how managed service providers (MSPs) and IT professionals can effectively navigate the increasingly complex landscape of regulatory requirements. By automating tasks like policy enforcement, vulnerability scanning, and reporting, these features not only streamline operations but also drastically reduce the risk of non-compliance, a threat that can carry substantial financial and reputational consequences. The ability to proactively manage and monitor compliance from a centralized platform offers unparalleled visibility and control, empowering organizations to maintain a strong security posture and demonstrate due diligence.
Ultimately, investing in premium RMM software with comprehensive compliance management capabilities is an investment in peace of mind. It allows IT teams to focus on strategic initiatives, knowing that their compliance obligations are being actively managed and monitored. We encourage you to explore the various RMM solutions available and carefully evaluate the compliance features they offer. Consider a free trial or request a demo to see firsthand how these powerful tools can transform your approach to compliance and security. Start your journey towards a more secure and compliant future today by researching which RMM best fits your needs, or by seeking consultation from an expert in the field.
Frequently Asked Questions (FAQ) about Compliance Management Features in Premium RMM Software
How can a premium RMM software help my business achieve and maintain compliance with industry regulations like HIPAA or GDPR?
Premium RMM (Remote Monitoring and Management) software offers a range of compliance management features that streamline the process of meeting industry regulations such as HIPAA (Health Insurance Portability and Accountability Act) or GDPR (General Data Protection Regulation). These features include automated patch management to ensure systems are up-to-date with the latest security updates, reducing vulnerabilities. RMMs also offer robust reporting capabilities, allowing you to easily generate audit logs and compliance reports demonstrating adherence to specific requirements. Furthermore, features like endpoint encryption, data loss prevention (DLP), and access control management help protect sensitive data, a critical aspect of both HIPAA and GDPR compliance. By automating many manual tasks and providing comprehensive visibility into your IT environment, RMM software significantly simplifies the path to regulatory compliance and reduces the risk of costly penalties. The best RMMs include built-in templates and policies to guide configuration and reporting.
What specific reporting and alerting capabilities related to compliance are typically included in premium RMM software solutions?
Premium RMM solutions provide extensive reporting and alerting features designed to monitor and manage compliance status. These capabilities often include pre-built reports tailored to specific regulations like PCI DSS, HIPAA, and GDPR, detailing areas of compliance and non-compliance across your IT infrastructure. Alerting mechanisms are crucial, enabling real-time notifications when deviations from compliance standards are detected. For example, an alert might trigger if a system is missing a critical security patch required for PCI compliance or if unauthorized access attempts are made on a server containing protected health information (PHI) under HIPAA. Some RMMs also offer automated remediation actions based on these alerts, such as automatically installing missing patches or disabling compromised accounts. Detailed audit trails, documenting all system changes and user activities, are also a standard feature, providing a comprehensive record for compliance audits. Moreover, custom reporting and alerting can be configured to address the unique needs of an organization.
How does using a premium RMM platform enhance the security posture of my endpoints to better support compliance requirements?
A premium RMM platform significantly strengthens the security posture of endpoints, directly supporting compliance efforts. RMMs automate patch management, ensuring all endpoints have the latest security updates, addressing vulnerabilities that could be exploited to compromise sensitive data. They also provide centralized management of antivirus and anti-malware software, ensuring consistent protection across all devices. Advanced threat detection capabilities, including behavioral analysis and intrusion detection, help identify and mitigate potential security breaches in real-time. Furthermore, RMMs facilitate the enforcement of security policies, such as password complexity requirements and access control restrictions, across all endpoints. Features like remote wipe and device encryption further protect data in the event of loss or theft. By proactively managing and securing endpoints, RMM platforms minimize the risk of security incidents that could lead to compliance violations and data breaches. This proactive approach to security is paramount for meeting the stringent requirements of regulations like GDPR and HIPAA.