In today’s complex IT landscape, securing endpoints is no longer a nice-to-have; it’s a necessity. We’re constantly battling a barrage of threats, from sophisticated ransomware attacks to sneaky phishing campaigns. Managing these threats effectively requires a robust endpoint protection strategy, and that’s where integrating your endpoint protection platform (EPP) with your Remote Monitoring and Management (RMM) system becomes a game-changer. It’s about more than just ticking boxes; it’s about creating a unified, proactive security posture.
Think of your RMM as your IT command center. It’s where you monitor your clients’ entire infrastructure, manage patches, automate tasks, and troubleshoot issues. Now, imagine being able to see the security status of every endpoint directly within that same console, deploy security updates with a single click, and automatically respond to threats as they emerge. That’s the power of integration. It streamlines your workflows, reduces response times, and ultimately, strengthens your clients’ defenses.

This article will delve into the specifics of endpoint protection integration with RMM systems. We’ll explore the benefits, the key features to look for, the challenges you might face, and how to overcome them. Whether you’re a seasoned MSP or a small IT team, understanding this integration is crucial for providing comprehensive and efficient security services. Let’s dive in and explore how you can leverage this powerful combination to protect your clients and streamline your operations.
What is Endpoint Protection and Why is it Important?
Endpoint protection refers to the practice of securing devices that connect to a network from threats. These devices, or endpoints, include desktops, laptops, servers, smartphones, and tablets. In essence, it’s about defending the perimeter of your network, one device at a time.
The Evolution of Endpoint Protection
Endpoint protection has evolved significantly over the years. It started with basic antivirus software, focused primarily on detecting and removing known malware. Today, endpoint protection platforms (EPPs) are far more sophisticated, incorporating a range of technologies such as:
- Antivirus/Antimalware: Still a core component, but now more advanced with behavioral analysis and machine learning.
- Firewall: Controls network traffic and prevents unauthorized access.
- Intrusion Detection/Prevention Systems (IDS/IPS): Monitors network traffic for malicious activity and blocks it.
- Endpoint Detection and Response (EDR): Continuously monitors endpoints for suspicious behavior and provides tools for investigation and remediation.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving the organization.
- Application Control: Restricts which applications can run on endpoints.
Why Endpoint Protection Matters
The importance of endpoint protection can’t be overstated. Here’s why:
- Protecting Sensitive Data: Endpoints often store or access sensitive data, making them prime targets for attackers.
- Preventing Malware Infections: Malware can disrupt operations, steal data, and damage reputation.
- Maintaining Compliance: Many regulations require organizations to implement endpoint protection measures.
- Reducing Downtime: Malware infections can lead to system downtime, impacting productivity and revenue.
- Protecting Brand Reputation: A security breach can damage an organization’s reputation and erode customer trust.
What is an RMM System and its Core Functionalities?
A Remote Monitoring and Management (RMM) system is a software platform used by IT professionals to remotely monitor and manage their clients’ or their own organization’s IT infrastructure. It’s the central hub for managing a distributed IT environment, providing visibility, control, and automation capabilities.
Key Features of an RMM System
RMM systems typically offer a wide range of features, including:
- Remote Monitoring: Real-time monitoring of system performance, hardware health, and software status.
- Patch Management: Automated patching of operating systems and applications to address vulnerabilities.
- Remote Access: Secure remote access to endpoints for troubleshooting and support.
- Automation: Scripting and automation capabilities to automate repetitive tasks.
- Alerting: Customizable alerts based on predefined thresholds and events.
- Reporting: Comprehensive reporting on system performance, security status, and other key metrics.
- Asset Management: Tracking of hardware and software assets.
- Service Desk Integration: Integration with service desk systems for ticket management.
Benefits of Using an RMM System
RMM systems offer numerous benefits, including:
- Improved Efficiency: Automating tasks and providing remote access reduces manual effort and improves efficiency.
- Proactive Problem Solving: Real-time monitoring and alerting allows for proactive identification and resolution of issues.
- Reduced Downtime: Early detection and remediation of problems minimizes downtime.
- Enhanced Security: Patch management and security monitoring helps to protect against threats.
- Centralized Management: A single pane of glass for managing the entire IT infrastructure.
- Scalability: RMM systems can easily scale to manage a growing number of endpoints.
Benefits of Integrating Endpoint Protection with RMM
The integration of endpoint protection and RMM systems creates a powerful synergy, offering significant benefits over using them as standalone solutions.
Centralized Management and Visibility
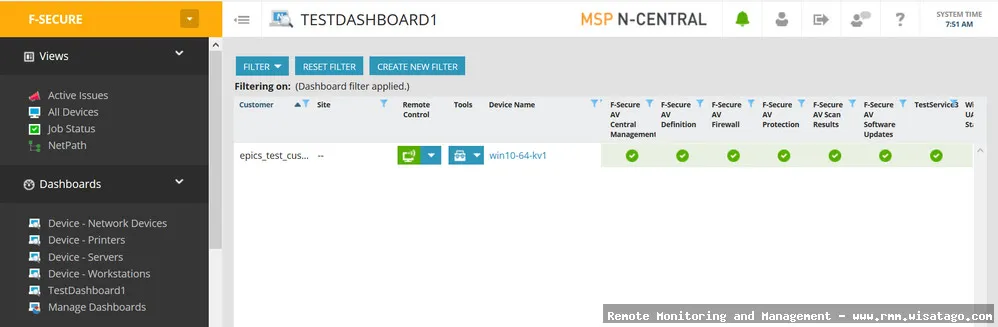
One of the biggest advantages is having a single console for managing both security and IT operations. Instead of switching between different platforms, you can see the security status of each endpoint directly within your RMM dashboard. This includes information such as:

- Antivirus status: Is it active, up-to-date, and scanning properly?
- Threat detections: What threats have been detected and remediated?
- Vulnerability status: Are there any known vulnerabilities on the endpoint?
- Patch status: Are all the necessary patches installed?
This centralized visibility allows for faster and more informed decision-making.
Automated Security Tasks
Integration enables you to automate many security tasks, such as:
- Deployment of security agents: Automatically deploy endpoint protection agents to new devices.
- Patch management: Automatically deploy security patches to address vulnerabilities.
- Threat remediation: Automatically isolate infected endpoints or remove malicious files.
- Policy enforcement: Enforce security policies across all endpoints.
Automation reduces manual effort, minimizes errors, and ensures consistent security across the entire environment.
Faster Incident Response
When a security incident occurs, speed is critical. Integration allows for faster incident response by:
- Real-time alerts: Receive immediate alerts when threats are detected.
- Remote access: Quickly access infected endpoints to investigate and remediate the issue.
- Isolation: Isolate infected endpoints to prevent the spread of malware.
Faster incident response minimizes the impact of security breaches and reduces downtime.
Improved Security Posture
By combining the capabilities of endpoint protection and RMM systems, you can significantly improve your overall security posture. This includes:
- Proactive threat detection: Identify and address threats before they cause damage.
- Reduced attack surface: Patch vulnerabilities and enforce security policies to reduce the attack surface.
- Enhanced compliance: Meet regulatory requirements by implementing comprehensive endpoint protection measures.
Key Features to Look for in an Integrated Solution
When choosing an endpoint protection solution that integrates with your RMM system, consider the following key features:
Seamless Integration
The integration should be seamless and easy to configure. Look for solutions that offer native integration or well-documented APIs.
Comprehensive Threat Protection
The endpoint protection solution should provide comprehensive threat protection, including:

- Antivirus/Antimalware: Protection against a wide range of malware threats.
- Advanced Threat Detection: Behavioral analysis and machine learning to detect unknown threats.
- Endpoint Detection and Response (EDR): Continuous monitoring and threat hunting capabilities.
Automated Patch Management
Automated patch management is crucial for addressing vulnerabilities. The solution should be able to automatically deploy patches for operating systems and applications.
Centralized Reporting and Analytics
The solution should provide centralized reporting and analytics, allowing you to track security metrics and identify trends.
Remote Management Capabilities
The solution should offer remote management capabilities, allowing you to manage endpoints remotely, even when they are not connected to the network.
Customizable Policies
The solution should allow you to customize security policies to meet the specific needs of your clients.
Challenges and Considerations
While integrating endpoint protection with RMM offers numerous benefits, it’s important to be aware of the potential challenges and considerations.
Compatibility Issues
Ensure that the endpoint protection solution is compatible with your RMM system. Not all solutions integrate seamlessly, and compatibility issues can lead to problems.
Complexity
Implementing and managing an integrated solution can be complex. You may need to invest in training and resources to ensure that your team has the necessary skills.
Cost
The cost of an integrated solution can be higher than using standalone solutions. Consider the total cost of ownership, including licensing, implementation, and maintenance.
Data Security and Privacy
Ensure that the solution complies with data security and privacy regulations. You need to protect your clients’ data and maintain their trust.
. For more information, you can refer to RMM as an additional resource.
Vendor Selection
Choosing the right vendor is crucial. Research different vendors, read reviews, and ask for references before making a decision.
Best Practices for Implementation
To ensure a successful implementation, follow these best practices:
Plan Carefully
Develop a detailed implementation plan that outlines your goals, timelines, and resources. Consider the specific needs of your clients and tailor the solution accordingly.
Test Thoroughly
Before deploying the solution to your entire environment, test it thoroughly in a pilot environment. This will help you identify and resolve any issues before they impact your clients.
Train Your Team
Provide your team with the necessary training to manage and support the integrated solution. Ensure that they understand the features, capabilities, and troubleshooting procedures.
Monitor Performance
Continuously monitor the performance of the solution to ensure that it is working as expected. Track key metrics and identify any areas for improvement.
Stay Up-to-Date
Keep the solution up-to-date with the latest patches and updates. This will help to protect against new threats and ensure that the solution is performing optimally.
Conclusion
Integrating endpoint protection with your RMM system is a strategic move that can significantly enhance your security posture, streamline your operations, and improve your overall efficiency. By centralizing management, automating tasks, and enabling faster incident response, you can provide your clients with a higher level of protection and peace of mind. While there are challenges to consider, the benefits of integration far outweigh the risks. By carefully planning your implementation, choosing the right vendor, and following best practices, you can leverage this powerful combination to protect your clients and grow your business.
Conclusion
In conclusion, endpoint protection integration with RMM systems offers a powerful synergy that significantly enhances IT management and security posture. By centralizing control, automating tasks, and providing real-time visibility across all endpoints, organizations can proactively defend against evolving cyber threats and streamline their IT operations. The benefits, ranging from improved threat detection and response to reduced operational costs and enhanced compliance, make a compelling case for adopting this integrated approach. The efficiencies gained allow IT professionals to focus on strategic initiatives rather than being bogged down in reactive firefighting.
The modern threat landscape demands a proactive and unified security strategy. Integrating your endpoint protection solution with your RMM system is no longer a luxury, but a necessity for maintaining a resilient and secure environment. If you’re looking to optimize your IT security and management capabilities, we strongly encourage you to explore the possibilities of endpoint protection integration. Contact your RMM and endpoint protection vendors today to learn more about available integrations and how they can benefit your organization. You can also visit our website at https://www.example.com/endpoint-integration for more information and resources.
Frequently Asked Questions (FAQ) about Endpoint Protection Integration with RMM Systems
What are the key benefits of integrating my endpoint protection software with my Remote Monitoring and Management (RMM) platform?
Integrating your endpoint protection solution with your RMM system offers several significant advantages. Firstly, it provides centralized management, allowing you to monitor and manage the security status of all endpoints directly from your RMM dashboard. This eliminates the need to switch between different consoles, saving time and improving efficiency. Secondly, integration enables automated threat response. Your RMM can be configured to automatically isolate infected endpoints, initiate scans, and deploy patches based on alerts from your endpoint protection software. This proactive approach minimizes the impact of security incidents. Finally, it enhances reporting and compliance. Integrated systems provide comprehensive reports on endpoint security posture, allowing you to demonstrate compliance with industry regulations and identify areas for improvement.
How does integrating endpoint protection with RMM help improve my cybersecurity posture and reduce the risk of malware infections?
Integrating endpoint protection with your RMM platform significantly strengthens your cybersecurity posture in several ways. The centralized visibility offered by the integration allows for proactive monitoring and identification of potential threats across all managed endpoints. Automated patching capabilities within the RMM, triggered by vulnerabilities detected by the endpoint protection, ensure that systems are quickly updated with the latest security fixes, reducing the attack surface. Furthermore, integrated threat intelligence feeds shared between the two platforms enable faster and more accurate detection of malware and other malicious activities. Automated remediation workflows, such as quarantining infected devices and removing malicious files, further minimize the impact of successful attacks, leading to a more robust and resilient security environment. By streamlining security operations and automating key tasks, this integration helps reduce the risk of costly malware infections and data breaches.
What are the common challenges when integrating endpoint protection with an RMM solution, and how can I overcome them?
Integrating endpoint protection with an RMM solution can present several challenges. One common issue is compatibility. Not all endpoint protection solutions are fully compatible with every RMM platform. Thorough research and testing are crucial to ensure seamless integration. Another challenge is configuration complexity. Setting up the integration and configuring the necessary policies and alerts can be complex and time-consuming. Utilizing vendor-provided documentation, training resources, and potentially engaging professional services can help overcome this. Data synchronization issues can also arise, leading to inaccurate reporting or delayed alerts. Implementing robust monitoring and troubleshooting processes to identify and resolve synchronization problems promptly is essential. Finally, permissions management is crucial. Carefully defining and managing user roles and permissions within both systems helps prevent unauthorized access and ensures data security. By addressing these challenges proactively, you can ensure a successful and beneficial integration.