Navigating the complex landscape of IT management in Europe requires not only robust technology but also a deep understanding of regulatory compliance. One of the most significant regulations impacting businesses is the General Data Protection Regulation (GDPR). For IT professionals, this means that the tools they use, including Remote Monitoring and Management (RMM) solutions, must be GDPR compliant. But what does that actually mean in practice? And how do you ensure your RMM solution is up to the task?
This article will delve into the GDPR compliance features that should be present in European RMM solutions. We’ll explore the key aspects of GDPR, examine how RMM solutions can help you achieve compliance, and highlight specific features to look for when choosing a solution. Think of this as a guide to help you make informed decisions and avoid potential legal pitfalls.

Forget the dry legal jargon for a moment. We’re going to break down the GDPR requirements and translate them into practical features and capabilities that you can assess in your RMM tool. Whether you’re a seasoned IT manager or just starting to explore RMM solutions, this guide will provide you with the knowledge you need to select a GDPR-compliant solution and protect your organization’s data.
Understanding GDPR and Its Impact on RMM Solutions
The General Data Protection Regulation (GDPR) is a regulation in EU law on data protection and privacy in the European Union (EU) and the European Economic Area (EEA). It also addresses the transfer of personal data outside the EU and EEA areas. The GDPR aims primarily to give control to individuals over their personal data and to simplify the regulatory environment for international business by unifying the regulation within the EU.
Key Principles of GDPR Relevant to RMM
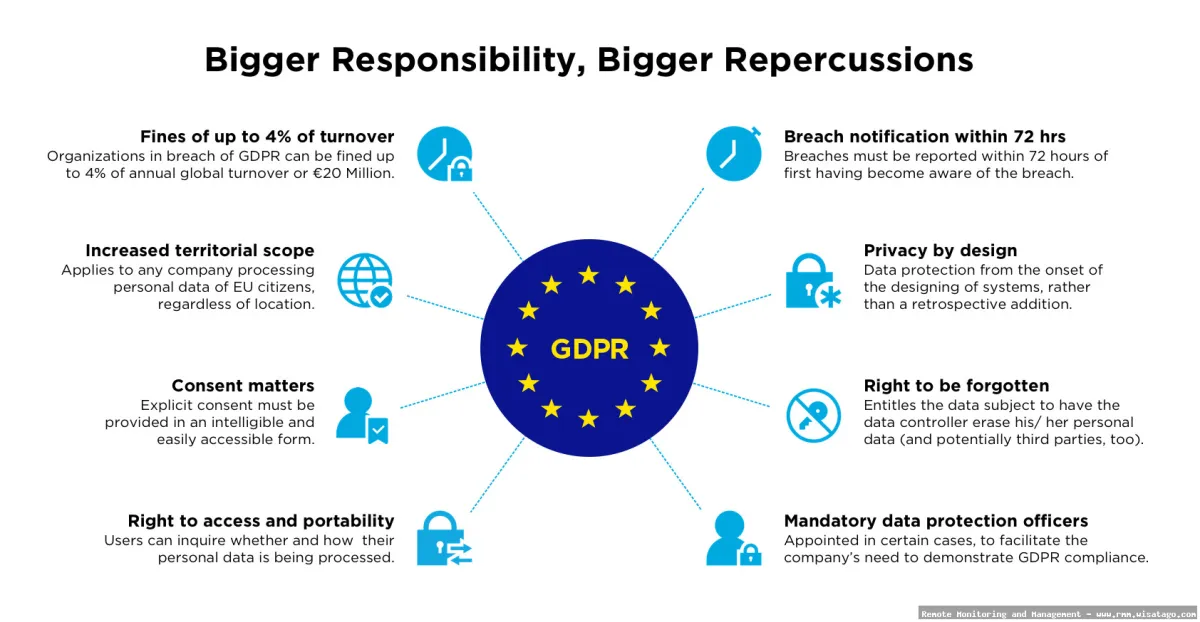
Understanding the core principles of GDPR is essential for evaluating the compliance of your RMM solution. Here are some key principles that directly impact how RMM systems handle data:
- Lawfulness, Fairness, and Transparency: Data processing must be lawful, fair, and transparent to the data subject. In the context of RMM, this means clearly informing clients about the data collected, how it’s used, and who has access to it.
- Purpose Limitation: Data can only be collected for specified, explicit, and legitimate purposes. RMM solutions should only collect data necessary for the intended purpose of monitoring and managing systems.
- Data Minimization: Only data that is adequate, relevant, and limited to what is necessary for the purpose should be processed. RMM solutions should avoid collecting unnecessary personal data.
- Accuracy: Data must be accurate and kept up to date. RMM solutions need to ensure that the data they collect is accurate and that mechanisms are in place to correct inaccuracies.
- Storage Limitation: Data should only be kept for as long as necessary for the purpose. RMM solutions must have clear data retention policies and procedures for securely deleting data when it’s no longer needed.
- Integrity and Confidentiality: Data must be processed in a manner that ensures appropriate security, including protection against unauthorized or unlawful processing, and against accidental loss, destruction, or damage. RMM solutions must implement robust security measures to protect data from unauthorized access and breaches.
- Accountability: The data controller is responsible for demonstrating compliance with the GDPR principles. IT teams must be able to demonstrate that their RMM solution is used in a GDPR-compliant manner.
Why GDPR Compliance is Crucial for RMM
RMM solutions often collect and process sensitive data, including:
- Device information (e.g., IP addresses, MAC addresses, device names)
- User account information
- Software inventory
- Performance data
- Security logs
This data can potentially identify individuals and therefore falls under the scope of GDPR. Non-compliance can result in significant fines, reputational damage, and legal action. Choosing a GDPR-compliant RMM solution is not just a matter of ticking a box; it’s about protecting your clients’ data and ensuring the long-term sustainability of your business.

GDPR Compliance Features to Look for in European RMM Solutions
So, what specific features should you look for when evaluating RMM solutions for GDPR compliance? Here’s a breakdown of essential features:
Data Residency and Location
One of the most important aspects of GDPR compliance is knowing where your data is stored. GDPR requires that data belonging to EU citizens remains within the EU or in countries with equivalent data protection laws. Therefore, your RMM solution should offer:
- EU-Based Data Centers: The ability to store data within the EU. This ensures that your data is subject to EU data protection laws.
- Data Residency Options: The flexibility to choose the specific location within the EU where your data is stored.
- Transparency: Clear information about the location of data storage and processing.
Data Encryption
Data encryption is a fundamental security measure that protects data from unauthorized access. Your RMM solution should employ encryption both in transit and at rest:
- Encryption in Transit: Using protocols like HTTPS and TLS to encrypt data as it’s transmitted between devices and servers.
- Encryption at Rest: Encrypting data when it’s stored on servers, using strong encryption algorithms.
Access Controls and Permissions
GDPR requires that access to personal data is restricted to authorized personnel only. Your RMM solution should provide granular access controls and permission management features:
- Role-Based Access Control (RBAC): Assigning different levels of access based on job roles.
- Multi-Factor Authentication (MFA): Requiring users to provide multiple forms of authentication to access the system.
- Audit Logging: Tracking user activity and access to data, providing an audit trail for compliance purposes.
Data Minimization and Retention Policies
As mentioned earlier, data minimization is a key principle of GDPR. Your RMM solution should help you minimize the amount of data collected and retain it only for as long as necessary:

- Configurable Data Collection: The ability to customize the types of data collected and disable the collection of unnecessary data.
- Data Retention Policies: Defining and enforcing data retention periods, automatically deleting data when it’s no longer needed.
- Data Anonymization and Pseudonymization: Techniques for masking or removing identifying information from data, reducing the risk of re-identification.
Data Subject Rights Management
GDPR grants individuals certain rights regarding their personal data, including the right to access, rectify, erase, restrict processing, and data portability. Your RMM solution should provide features to help you manage these rights:
- Data Access Requests: Tools for easily retrieving and providing individuals with access to their data.
- Data Rectification: Mechanisms for correcting inaccurate or incomplete data.
- Data Erasure (Right to be Forgotten): Procedures for securely deleting data at the request of an individual.
- Data Portability: Functionality for exporting data in a structured, commonly used format, allowing individuals to transfer their data to another provider.
Data Breach Notification
In the event of a data breach, GDPR requires that you notify the relevant authorities and affected individuals within a specific timeframe. Your RMM solution should provide features to help you detect, investigate, and report data breaches:
- Security Monitoring and Alerts: Real-time monitoring of system activity and alerts for suspicious behavior.
- Incident Response Tools: Tools for investigating and responding to security incidents.
- Breach Notification Templates: Pre-built templates for notifying authorities and individuals in the event of a breach.
Compliance Documentation and Support
Finally, your RMM vendor should provide comprehensive documentation and support to help you achieve GDPR compliance:
- GDPR Compliance Documentation: Detailed documentation outlining the vendor’s GDPR compliance measures.
- Data Processing Agreements (DPAs): A legally binding agreement between you and the vendor that outlines the responsibilities of each party regarding data protection.
- Dedicated Support: Access to support staff who are knowledgeable about GDPR and can assist you with compliance-related questions.
Challenges in Implementing GDPR-Compliant RMM Solutions
While selecting a GDPR-compliant RMM solution is a crucial first step, implementing it effectively can present several challenges:
Data Discovery and Mapping
Identifying and mapping all the data that your RMM solution collects and processes can be a complex task. You need to understand what data is collected, where it’s stored, how it’s used, and who has access to it. This requires a thorough assessment of your RMM solution’s capabilities and your organization’s data flows.

Integrating with Existing Systems
RMM solutions often integrate with other systems, such as ticketing systems, CRM systems, and security tools. Ensuring that these integrations are also GDPR compliant can be challenging. You need to review the data sharing practices of each integrated system and ensure that data is protected throughout the entire data lifecycle.
Training and Awareness
Even with a GDPR-compliant RMM solution in place, it’s essential to train your IT staff on GDPR principles and best practices. They need to understand how to use the RMM solution in a compliant manner and how to respond to data subject requests. Regular training and awareness programs are crucial for maintaining ongoing compliance.
Ongoing Monitoring and Auditing
GDPR compliance is not a one-time effort; it’s an ongoing process. You need to continuously monitor your RMM solution’s performance, audit its data processing practices, and update your policies and procedures as needed. Regular audits can help you identify potential compliance gaps and ensure that your RMM solution remains GDPR compliant over time.
Choosing the Right European RMM Solution for GDPR Compliance
Selecting the right RMM solution is critical for ensuring GDPR compliance. Here are some key considerations to keep in mind during your evaluation:
- Vendor Reputation and Experience: Choose a vendor with a proven track record of GDPR compliance and experience working with European businesses.
- Feature Set: Ensure that the RMM solution offers all the essential GDPR compliance features, such as data residency, encryption, access controls, data retention policies, and data subject rights management.
- Scalability: Select a solution that can scale to meet your organization’s growing needs and adapt to evolving GDPR requirements.
- Cost: Consider the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance.
- Ease of Use: Choose a solution that is easy to use and manage, allowing your IT staff to effectively implement and maintain GDPR compliance.
Conclusion
GDPR compliance is a critical consideration for any organization operating in Europe, and your RMM solution plays a vital role in achieving compliance. By understanding the key principles of GDPR and selecting an RMM solution with the right features, you can protect your clients’ data, avoid potential fines, and maintain a strong reputation. Remember to prioritize data residency, encryption, access controls, data retention policies, and data subject rights management when evaluating RMM solutions. Invest in training and awareness programs for your IT staff and continuously monitor your RMM solution to ensure ongoing GDPR compliance. By taking these steps, you can confidently leverage the power of RMM while meeting your GDPR obligations.
. Effective IT management often involves various tools, and RMM is one such solution used to remotely monitor and manage client systems
.
Conclusion
In conclusion, navigating the intricacies of GDPR compliance while effectively managing IT infrastructure requires a strategic approach. As we’ve explored, European RMM solutions are increasingly equipped with features designed to aid in this crucial task, offering functionalities like robust data encryption, granular access control, detailed audit trails, and automated data discovery. These features, while not a silver bullet, are essential components in building a GDPR-compliant IT environment. Ignoring these capabilities and their potential benefits could expose organizations to significant legal and financial risks, as well as reputational damage.
The GDPR landscape is constantly evolving, and so too must the tools and strategies employed to maintain compliance. Choosing an RMM solution that prioritizes GDPR compliance is no longer optional, but a necessity for any organization operating within the EU. We encourage you to thoroughly evaluate your current RMM solution or, if you’re seeking a new one, to carefully consider the GDPR compliance features offered. Remember, a proactive approach to data protection is not just about adhering to regulations; it’s about building trust with your clients and stakeholders. Learn more about specific RMM solutions and their GDPR capabilities by visiting our RMM Comparison Guide.
Frequently Asked Questions (FAQ) about GDPR Compliance Features in European RMM Solutions
What specific GDPR compliance features should I look for when choosing a European RMM (Remote Monitoring and Management) solution to ensure data protection?
When selecting a European RMM solution with GDPR compliance in mind, several key features are crucial. Firstly, look for robust data encryption both in transit and at rest, ensuring that sensitive client data is protected from unauthorized access. Secondly, the RMM should offer granular access control, allowing you to define precisely who can access which data and functionalities. Thirdly, a comprehensive audit logging system is vital for tracking data access and modifications, providing accountability and facilitating investigations in case of a breach. Fourthly, the ability to easily anonymize or pseudonymize data can be extremely beneficial. Finally, ensure the RMM vendor offers a clear Data Processing Agreement (DPA) that outlines their responsibilities and commitments regarding GDPR compliance. Checking for these features helps ensure that your chosen RMM aligns with the requirements of GDPR.
How do European RMM solutions help me comply with GDPR’s “right to be forgotten” (data erasure) requests from my clients, and what are the best practices for handling these requests within the RMM platform?
European RMM solutions can assist with the “right to be forgotten” (data erasure) requests by providing functionalities to identify, locate, and permanently delete all personal data related to a specific client. This includes data stored within the RMM’s database, logs, and backups. Best practices for handling these requests involve establishing a clear and documented process. Firstly, verify the identity of the requester. Secondly, use the RMM’s search and reporting tools to identify all instances of the client’s data. Thirdly, securely and permanently delete the data, ensuring that it cannot be recovered. Fourthly, document the deletion process and maintain an audit trail. Finally, confirm the completion of the request with the client. Choosing an RMM with automated data deletion capabilities can significantly streamline this process and minimize the risk of non-compliance. Remember to consult with legal counsel to ensure your procedures fully align with GDPR requirements.
What kind of data security certifications, such as ISO 27001, should I look for in a European RMM vendor to ensure they are taking data protection seriously and are compliant with GDPR requirements?
When evaluating European RMM vendors for GDPR compliance, it’s crucial to consider their data security certifications. ISO 27001 is a widely recognized international standard for Information Security Management Systems (ISMS) and demonstrates a vendor’s commitment to establishing, implementing, maintaining, and continually improving their information security practices. SOC 2 Type II is another important certification, demonstrating that the vendor has controls in place to protect customer data based on security, availability, processing integrity, confidentiality, and privacy. GDPR certifications, while still evolving, specifically assess a vendor’s adherence to GDPR principles. Having these certifications indicates that the RMM vendor has undergone independent audits and has implemented robust security measures to protect data. It’s also beneficial to inquire about their adherence to other relevant security frameworks and their data breach notification procedures. Choose a vendor with strong security credentials to minimize your risk and ensure compliance with GDPR.