In today’s hyper-connected world, mobile devices are no longer just communication tools; they are integral components of enterprise operations. Employees use smartphones and tablets for everything from accessing company emails and sensitive data to managing customer relationships and processing transactions. This widespread adoption, while boosting productivity and flexibility, also presents significant challenges for IT departments. How do you secure, manage, and monitor all these devices effectively, especially when they’re scattered across different locations and potentially used for both work and personal purposes? That’s where Enterprise Mobile Device Management (EMDM) comes in, and increasingly, it’s being integrated with Remote Monitoring and Management (RMM) platforms to streamline operations and enhance security.
Think of it this way: your RMM platform is your central command center for all your IT assets – servers, desktops, laptops, network devices, and now, mobile devices. By extending the capabilities of your RMM to include MDM features, you gain a unified view of your entire IT landscape, allowing you to proactively identify and resolve issues, enforce security policies, and ensure compliance across all endpoints. It’s about bringing order to the chaos of a rapidly expanding mobile ecosystem within your organization.
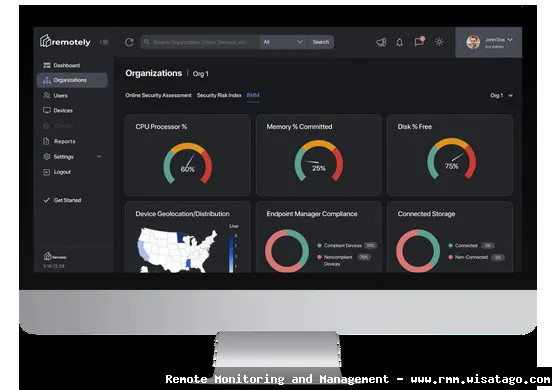
This article dives deep into the world of Enterprise Mobile Device Management via RMM. We’ll explore the core functionalities, benefits, and challenges of this integrated approach. We’ll examine the specific features you should look for in an RMM platform with robust MDM capabilities, and discuss how to implement and manage this solution effectively. Whether you’re a seasoned IT professional looking to optimize your existing RMM setup or a business owner exploring options for managing your growing mobile workforce, this guide will provide the insights you need to make informed decisions and navigate the complexities of modern mobile device management.
Understanding Enterprise Mobile Device Management (EMDM)
Enterprise Mobile Device Management (EMDM) is a comprehensive approach to managing and securing mobile devices within an organization. It encompasses a wide range of functionalities designed to ensure that company data remains protected, devices are compliant with policies, and users have the necessary access to perform their jobs efficiently.
Key Objectives of EMDM
The primary goals of EMDM can be summarized as follows:
- Security: Protecting sensitive company data from unauthorized access, loss, or theft.
- Compliance: Enforcing policies and regulations to ensure devices and users adhere to industry standards and legal requirements.
- Management: Streamlining the deployment, configuration, and maintenance of mobile devices.
- Productivity: Enabling users to access the resources they need to be productive, while maintaining security and control.
Core EMDM Features
EMDM solutions typically offer a variety of features, including:
- Device Enrollment: Securely enrolling devices into the management system, often using methods like Apple Business Manager (ABM), Android Enterprise, or manual enrollment.
- Configuration Management: Configuring device settings, such as email accounts, Wi-Fi networks, VPN settings, and security policies.
- Application Management: Deploying, updating, and removing applications on managed devices. This includes both public apps from app stores and private, custom-built apps.
- Security Policy Enforcement: Enforcing security policies, such as password complexity requirements, encryption, and remote wipe capabilities.
- Remote Monitoring and Control: Monitoring device status, usage, and security posture, and remotely troubleshooting issues.
- Geolocation Tracking: Tracking the location of devices, which can be useful for asset management and security purposes.
- Reporting and Analytics: Generating reports on device usage, security compliance, and other key metrics.
The Power of RMM: A Centralized Management Platform
Remote Monitoring and Management (RMM) platforms are the backbone of modern IT management. They provide IT professionals with a centralized dashboard to monitor, manage, and support a wide range of IT assets, including servers, desktops, laptops, and network devices. Integrating EMDM into an RMM platform extends these capabilities to mobile devices, creating a unified management solution.
Benefits of Using RMM for EMDM
Integrating EMDM with an RMM platform offers several significant advantages:

- Centralized Management: A single pane of glass for managing all IT assets, including mobile devices, simplifying workflows and reducing administrative overhead.
- Proactive Monitoring: Real-time monitoring of device health, security status, and compliance, enabling proactive identification and resolution of issues.
- Automated Tasks: Automating routine tasks, such as software updates, security patching, and configuration changes, freeing up IT staff to focus on more strategic initiatives.
- Improved Security: Enhanced security posture through consistent policy enforcement, vulnerability management, and threat detection across all devices.
- Simplified Compliance: Streamlined compliance management with centralized reporting and auditing capabilities.
- Cost Savings: Reduced IT costs through improved efficiency, proactive problem solving, and automated tasks.
How RMM Enhances EMDM Capabilities
RMM platforms bring several key enhancements to EMDM:
- Remote Access and Control: RMM tools often include remote access capabilities, allowing IT staff to remotely troubleshoot and resolve issues on mobile devices.
- Scripting and Automation: RMM platforms allow IT staff to create custom scripts and automated workflows to manage mobile devices in bulk.
- Integration with Other Tools: RMM platforms often integrate with other IT management tools, such as ticketing systems, security information and event management (SIEM) solutions, and asset management systems.
- Alerting and Notifications: RMM platforms provide alerting and notification capabilities, allowing IT staff to be alerted to critical issues on mobile devices.
Key Features to Look for in an RMM with EMDM Capabilities
Not all RMM platforms offer the same level of EMDM functionality. When evaluating RMM solutions, it’s crucial to look for specific features that will enable you to effectively manage your mobile devices.
Essential EMDM Features within RMM
Here are some key features to consider:
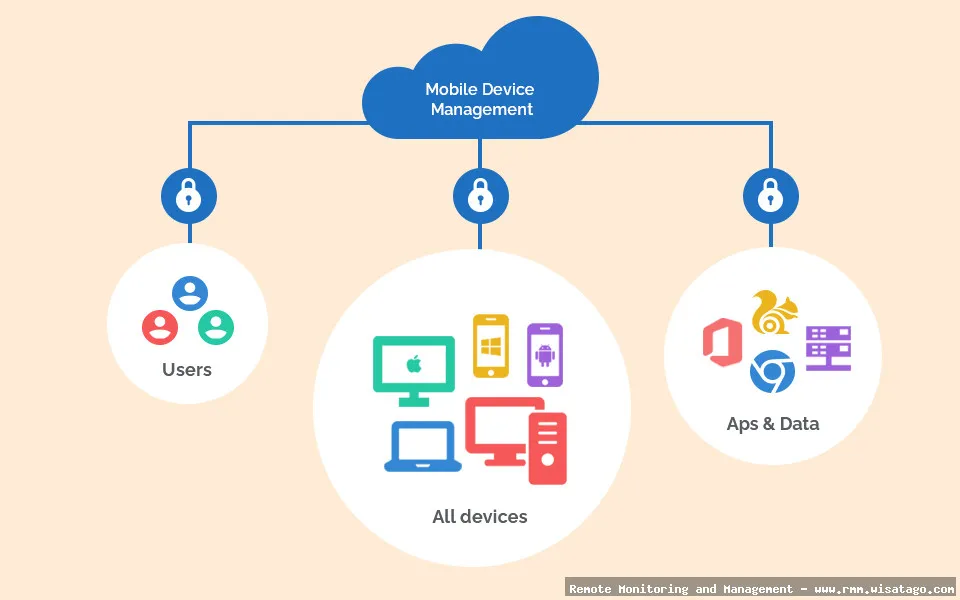
- Cross-Platform Support: The RMM should support a wide range of mobile operating systems, including iOS, Android, and potentially others depending on your organization’s needs.
- Device Enrollment Options: The RMM should offer various enrollment methods, such as Apple Business Manager (ABM), Android Enterprise, and manual enrollment, to accommodate different device types and deployment scenarios.
- Application Management: The RMM should provide robust application management capabilities, including the ability to deploy, update, and remove apps, manage app licenses, and control app usage.
- Security Policy Enforcement: The RMM should allow you to define and enforce security policies, such as password complexity requirements, encryption, and remote wipe capabilities.
- Compliance Management: The RMM should provide tools to track and report on device compliance with security policies and industry regulations.
- Remote Monitoring and Troubleshooting: The RMM should offer remote monitoring and troubleshooting capabilities, allowing you to identify and resolve issues on mobile devices remotely.
- Geolocation Tracking: The RMM should provide geolocation tracking capabilities, allowing you to track the location of devices for asset management and security purposes.
- Reporting and Analytics: The RMM should provide comprehensive reporting and analytics capabilities, allowing you to track device usage, security compliance, and other key metrics.
- Integration with Existing Infrastructure: The RMM should integrate seamlessly with your existing IT infrastructure, including your Active Directory, email servers, and other critical systems.
Implementing and Managing EMDM via RMM: Best Practices
Implementing and managing EMDM via RMM requires careful planning and execution. Here are some best practices to ensure a successful deployment:
Planning and Preparation
- Define Clear Objectives: Clearly define your goals for EMDM. What are you trying to achieve? (e.g., improve security, enhance compliance, streamline management).
- Assess Your Needs: Identify the specific requirements of your organization, including the types of devices you need to manage, the security policies you need to enforce, and the compliance regulations you need to adhere to.
- Choose the Right RMM Solution: Select an RMM platform with robust EMDM capabilities that meets your specific needs. Consider factors such as cross-platform support, enrollment options, application management features, and security policy enforcement capabilities.
- Develop a Comprehensive Policy: Create a comprehensive mobile device policy that outlines acceptable use, security requirements, and compliance regulations.
- Pilot Program: Start with a pilot program to test your EMDM implementation and identify any potential issues before rolling it out to the entire organization.
Deployment and Configuration
- Device Enrollment: Enroll devices into the management system using the appropriate enrollment methods.
- Configuration Management: Configure device settings, such as email accounts, Wi-Fi networks, VPN settings, and security policies.
- Application Management: Deploy, update, and remove applications on managed devices.
- Security Policy Enforcement: Enforce security policies, such as password complexity requirements, encryption, and remote wipe capabilities.
- User Training: Provide users with training on how to use their devices securely and comply with company policies.
Ongoing Management and Monitoring
- Remote Monitoring: Continuously monitor device health, security status, and compliance.
- Regular Updates: Keep devices and applications up to date with the latest security patches and updates.
- Incident Response: Develop an incident response plan to address security breaches and other incidents.
- Policy Review: Regularly review and update your mobile device policy to ensure it remains relevant and effective.
- Reporting and Analytics: Generate reports on device usage, security compliance, and other key metrics to identify areas for improvement.
Challenges and Considerations
While EMDM via RMM offers significant benefits, it’s essential to be aware of the potential challenges and considerations:
Common Challenges
- User Privacy Concerns: Balancing security with user privacy can be a challenge. Be transparent with users about what data is being collected and how it is being used.
- Device Fragmentation: The diversity of mobile devices and operating systems can make management more complex.
- BYOD (Bring Your Own Device) Support: Managing BYOD devices requires careful consideration of security policies and user privacy.
- Integration Complexity: Integrating EMDM with existing IT infrastructure can be complex and require careful planning.
- Cost: Implementing and managing EMDM can be costly, especially for large organizations.
Mitigation Strategies
- Clear Communication: Communicate clearly with users about the benefits of EMDM and the security measures being implemented.
- Flexible Policies: Develop flexible security policies that accommodate different device types and user needs.
- Containerization: Use containerization technologies to separate personal and corporate data on BYOD devices.
- Thorough Planning: Plan your EMDM implementation carefully, considering all potential challenges and risks.
- Cost-Benefit Analysis: Conduct a cost-benefit analysis to determine the potential return on investment (ROI) of EMDM.
Conclusion: Embracing the Future of Mobile Device Management
Enterprise Mobile Device Management via RMM is no longer a luxury, but a necessity for organizations of all sizes. By integrating EMDM into your RMM platform, you can gain a centralized view of your entire IT landscape, proactively identify and resolve issues, enforce security policies, and ensure compliance across all endpoints. While there are challenges to consider, the benefits of improved security, enhanced productivity, and simplified management far outweigh the risks.

As mobile devices continue to play an increasingly important role in the workplace, embracing EMDM via RMM will be crucial for organizations looking to stay ahead of the curve and protect their valuable data. By carefully planning your implementation, choosing the right RMM solution, and adhering to best practices, you can successfully manage your mobile devices and unlock the full potential of your mobile workforce.
The future of IT management is unified and proactive. By combining the power of RMM with the capabilities of EMDM, you can create a secure, efficient, and manageable mobile environment that empowers your employees and protects your business. Effective IT management often necessitates a comprehensive approach, and RMM can be a valuable tool in achieving that goal
.
Conclusion
In conclusion, integrating Enterprise Mobile Device Management (EMM) capabilities within a Remote Monitoring and Management (RMM) platform offers a powerful synergy for modern IT management. By centralizing control over both traditional endpoints and mobile devices, organizations can significantly streamline operations, enhance security posture, and improve overall efficiency. We’ve seen how this integrated approach addresses the challenges of managing a diverse and increasingly mobile workforce, providing a unified view and control point that simplifies complex tasks like policy enforcement, application management, and security patching.
The benefits of this integration are undeniable, from reduced administrative overhead to improved data security and enhanced end-user productivity. As mobile devices become ever more integral to business operations, choosing an RMM solution that embraces EMM functionality is no longer just an option, but a necessity for staying ahead of the curve. If you are looking to optimize your IT management and secure your mobile workforce, we encourage you to explore the possibilities of integrating EMM within your existing RMM platform or to consider https://www.example.com/rmm-emm solutions that offer this combined functionality. Take control of your entire IT ecosystem today!
Frequently Asked Questions (FAQ) about Enterprise Mobile Device Management via RMM
How can I use my Remote Monitoring and Management (RMM) platform to manage and secure company-owned mobile devices, and what are the key benefits of this approach?
Leveraging your existing Remote Monitoring and Management (RMM) platform for enterprise mobile device management (MDM) allows you to centrally manage and secure company-owned mobile devices, streamlining IT operations. RMMs often offer features like remote device configuration, application deployment and management, security policy enforcement, and device tracking. Integrating MDM within your RMM provides a unified dashboard for managing all endpoints, including desktops, servers, and mobile devices. This reduces complexity, improves efficiency, and allows for faster response times to security threats. Key benefits include improved security posture through consistent policy enforcement, reduced IT overhead via centralized management, enhanced device visibility and control, and streamlined compliance reporting. This integrated approach simplifies device management and strengthens overall IT security.
What are the essential security features I should look for when choosing an RMM solution with mobile device management capabilities to protect sensitive company data on employee smartphones and tablets?
When selecting an RMM solution with mobile device management (MDM) features, prioritize security capabilities to protect sensitive data on employee devices. Essential features include remote wipe capabilities to erase data from lost or stolen devices, enforced passcode policies to prevent unauthorized access, and containerization to separate corporate data from personal data. Look for solutions that offer mobile threat defense (MTD) to detect and remediate malware, phishing attacks, and other mobile-specific threats. Furthermore, data loss prevention (DLP) features are crucial for preventing sensitive information from leaving the corporate environment. Finally, ensure the RMM solution supports encryption of data at rest and in transit to safeguard against data breaches. Selecting a robust MDM solution integrated with RMM provides a comprehensive security layer for your mobile workforce.
How does using an RMM platform for mobile device management help with compliance regulations such as GDPR, HIPAA, or CCPA, and what reporting features should I expect?
Employing an RMM platform for enterprise mobile device management (MDM) significantly aids in achieving and maintaining compliance with regulations like GDPR, HIPAA, and CCPA. These regulations mandate stringent data protection and privacy measures. MDM capabilities within an RMM allow you to enforce security policies, control data access, and track device usage, all critical for compliance. Expect reporting features that provide detailed insights into device security posture, data access logs, and policy compliance status. The RMM should generate reports demonstrating adherence to specific regulatory requirements, such as encryption status, password complexity, and data residency. Furthermore, the ability to remotely wipe devices containing sensitive data ensures compliance in case of loss or theft. By providing comprehensive visibility and control over mobile devices, RMM-integrated MDM simplifies the compliance process and reduces the risk of costly breaches and penalties.