In today’s complex IT landscape, managing and maintaining a company’s assets can feel like herding cats. From laptops and servers to software licenses and network devices, keeping track of everything is a monumental task. Without a robust system in place, you’re essentially flying blind, vulnerable to security breaches, compliance violations, and inefficient resource allocation. That’s where IT Asset Management (ITAM) comes in, and increasingly, Remote Monitoring and Management (RMM) software is proving to be the key to unlocking its full potential.
Think of RMM as your IT team’s eyes and ears across the entire network, constantly monitoring the health and performance of every device. But it’s more than just a monitoring tool. Modern RMM solutions offer a suite of features designed to streamline ITAM processes, automate tasks, and provide a centralized view of your entire IT estate. This allows IT professionals to proactively address issues, optimize resource utilization, and ensure that all assets are secure and compliant.

This article will delve into the world of IT Asset Management through RMM software. We’ll explore the core features of RMM that facilitate effective ITAM, discuss the benefits of integrating these two disciplines, and address the challenges that IT teams might encounter during implementation. Consider this your complete guide to understanding how RMM can transform your ITAM strategy from a reactive chore to a proactive advantage.
What is IT Asset Management (ITAM)?
IT Asset Management (ITAM) is the practice of systematically tracking and managing all of an organization’s IT assets throughout their lifecycle. This includes hardware, software, network devices, cloud resources, and even virtual machines. The goal of ITAM is to optimize the utilization, value, and security of these assets while minimizing risks and costs.
Key Components of ITAM
Effective ITAM involves several key components:
- Asset Discovery: Identifying and cataloging all IT assets within the organization’s environment.
- Asset Tracking: Monitoring the location, status, and ownership of each asset throughout its lifecycle.
- License Management: Ensuring compliance with software licensing agreements and optimizing software usage.
- Configuration Management: Maintaining accurate records of asset configurations and changes.
- Security Management: Protecting assets from unauthorized access and cyber threats.
- Lifecycle Management: Managing the entire lifecycle of an asset, from procurement to disposal.
What is Remote Monitoring and Management (RMM) Software?
Remote Monitoring and Management (RMM) software is a platform used by IT service providers (MSPs) and internal IT departments to remotely monitor, manage, and support their clients’ or employees’ IT systems. It provides a centralized console for monitoring the health, performance, and security of devices, automating tasks, and resolving issues remotely.
Core Features of RMM Software
RMM software typically includes the following core features:
- Remote Monitoring: Continuously monitoring the health and performance of devices, servers, and networks.
- Remote Access: Providing secure remote access to devices for troubleshooting and support.
- Patch Management: Automating the deployment of software updates and security patches.
- Automation: Automating routine tasks such as scripting, software deployment, and system maintenance.
- Alerting and Reporting: Providing real-time alerts for critical issues and generating reports on system performance.
- Asset Discovery and Inventory: Automatically discovering and inventorying IT assets on the network.
- Security Management: Offering security features such as antivirus, anti-malware, and vulnerability scanning.
How RMM Software Enhances IT Asset Management
RMM software significantly enhances ITAM by providing a centralized, automated, and proactive approach to managing IT assets. It bridges the gap between asset discovery, tracking, and maintenance, enabling IT teams to gain better visibility, control, and efficiency.
Automated Asset Discovery and Inventory
RMM software automatically discovers and inventories IT assets on the network, eliminating the need for manual data entry and reducing the risk of errors. This provides a comprehensive and up-to-date view of all hardware and software assets, including their configurations, installed software, and network connections.

Real-time Monitoring and Alerting
RMM software continuously monitors the health and performance of IT assets, providing real-time alerts for critical issues such as hardware failures, software errors, and security threats. This allows IT teams to proactively address problems before they impact users or business operations.
Software License Management
RMM software can track software installations and usage, helping organizations ensure compliance with software licensing agreements. By monitoring software usage, IT teams can identify underutilized licenses and reallocate them to other users, reducing software costs.
Patch Management and Vulnerability Scanning
RMM software automates the deployment of software updates and security patches, ensuring that all IT assets are protected against known vulnerabilities. Regular vulnerability scanning helps identify potential security weaknesses and allows IT teams to take corrective action before they are exploited.
Remote Access and Control
RMM software provides secure remote access to IT assets, allowing IT teams to troubleshoot issues, perform maintenance, and deploy software updates from anywhere. This reduces the need for on-site visits and improves response times.
Reporting and Analytics
RMM software generates reports on IT asset utilization, performance, and security. These reports provide valuable insights into the health of the IT infrastructure and help IT teams make informed decisions about resource allocation, capacity planning, and security investments.
Benefits of Integrating RMM and ITAM
Integrating RMM and ITAM provides numerous benefits to organizations, including:
Improved Visibility and Control
By combining the real-time monitoring and automation capabilities of RMM with the asset tracking and management features of ITAM, organizations gain complete visibility and control over their IT assets. This enables them to make better decisions about resource allocation, security, and compliance.
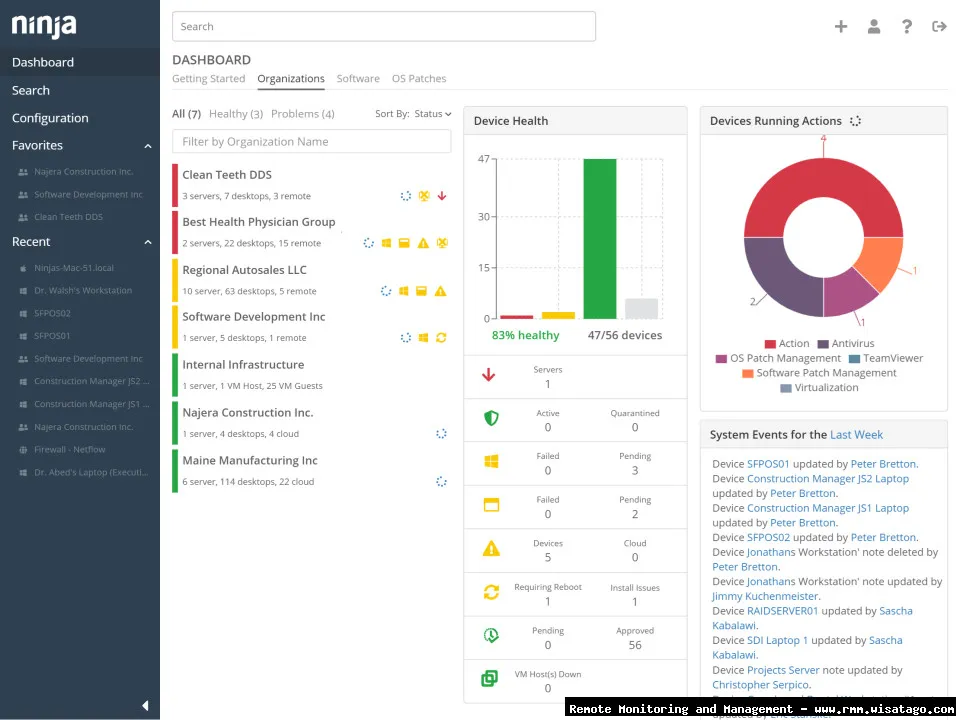
. Effective IT management often relies on a system, and RMM is one such solution designed to streamline these processes
.
Enhanced Security
RMM software’s patch management, vulnerability scanning, and security monitoring features help protect IT assets from cyber threats. By integrating RMM with ITAM, organizations can ensure that all assets are properly secured and compliant with security policies.
Reduced Costs
By optimizing asset utilization, automating tasks, and reducing downtime, integrating RMM and ITAM can significantly reduce IT costs. This includes savings on software licenses, hardware maintenance, and labor costs.
Increased Efficiency
RMM software automates many of the routine tasks associated with ITAM, such as asset discovery, software deployment, and patch management. This frees up IT staff to focus on more strategic initiatives.
Improved Compliance
RMM software helps organizations comply with regulatory requirements by providing detailed records of IT asset configurations, security settings, and software licenses. This simplifies audits and reduces the risk of non-compliance penalties.
Challenges of Implementing RMM for ITAM
While integrating RMM and ITAM offers significant benefits, there are also some challenges that IT teams may encounter during implementation:
Data Integration
Integrating RMM data with existing ITAM systems can be complex, especially if the systems use different data formats or schemas. Careful planning and data mapping are essential to ensure accurate and consistent data.
Training and Adoption
IT staff need to be trained on how to use the RMM software and how to integrate it with existing ITAM processes. This may require investing in training programs and providing ongoing support.

Cost
RMM software can be expensive, especially for large organizations with complex IT environments. IT teams need to carefully evaluate the costs and benefits of different RMM solutions before making a purchase.
Security Concerns
RMM software provides remote access to IT systems, which can create security vulnerabilities if not properly secured. Organizations need to implement strong security controls to protect their RMM platform from unauthorized access.
Best Practices for Implementing RMM for ITAM
To successfully implement RMM for ITAM, IT teams should follow these best practices:
Define Clear Goals and Objectives
Before implementing RMM, define clear goals and objectives for ITAM. What do you want to achieve with RMM? What metrics will you use to measure success? Having clear goals will help you choose the right RMM solution and implement it effectively.
Choose the Right RMM Solution
There are many different RMM solutions available, each with its own strengths and weaknesses. Choose a solution that meets your specific needs and budget. Consider factors such as the size of your organization, the complexity of your IT environment, and the features you need.
Develop a Detailed Implementation Plan
Develop a detailed implementation plan that outlines the steps involved in deploying RMM, integrating it with existing ITAM systems, and training IT staff. The plan should also include a timeline and budget.
Start Small and Scale Gradually
Don’t try to implement RMM across your entire organization at once. Start with a pilot project and gradually scale the implementation as you gain experience and confidence. This will help you identify and address any potential problems before they impact your entire organization.

Monitor and Evaluate Performance
Continuously monitor and evaluate the performance of your RMM implementation. Track key metrics such as asset utilization, security incidents, and downtime. Use this data to identify areas for improvement and optimize your RMM configuration.
Conclusion
IT Asset Management is no longer a nice-to-have; it’s a critical component of a well-managed IT infrastructure. By leveraging the power of RMM software, organizations can streamline their ITAM processes, improve security, reduce costs, and increase efficiency. While there are challenges to overcome, the benefits of integrating RMM and ITAM far outweigh the risks. By following best practices and carefully planning their implementation, IT teams can unlock the full potential of RMM and transform their ITAM strategy from a reactive chore to a proactive advantage, ensuring a secure, compliant, and optimized IT environment.
Conclusion
In summary, implementing IT Asset Management (ITAM) through Remote Monitoring and Management (RMM) software offers a powerful and integrated approach to managing your technology infrastructure. By leveraging the automation, centralized visibility, and proactive monitoring capabilities of RMM, organizations can significantly improve asset tracking, reduce operational costs, enhance security posture, and ensure compliance. The ability to remotely access and manage assets, coupled with detailed reporting and analytics, provides invaluable insights for informed decision-making and strategic IT planning.
The benefits of integrating ITAM with RMM are clear: greater efficiency, reduced risk, and optimized resource allocation. If your organization is seeking to gain better control over its IT assets and improve overall IT operations, exploring RMM solutions with robust ITAM features is a crucial step. Consider researching various RMM platforms and evaluating their capabilities in relation to your specific needs. Furthermore, many providers offer free trials or demos, allowing you to experience the advantages firsthand. Don’t delay in empowering your IT team with the tools they need to succeed; start exploring RMM-driven ITAM today and unlock the full potential of your IT assets.
Frequently Asked Questions (FAQ) about IT Asset Management Through RMM Software
How does using RMM software for IT asset management help to improve cybersecurity posture and reduce potential security risks?
Using RMM software for IT asset management significantly strengthens your cybersecurity posture. By providing a centralized view of all hardware and software assets, RMM allows for proactive identification of vulnerabilities. This includes identifying outdated operating systems, missing security patches, and unauthorized software installations, all of which can be exploited by cybercriminals. RMM enables automated patching and software updates, ensuring that systems are always running the latest security versions. Furthermore, the ability to remotely monitor asset health and performance allows for early detection of suspicious activity or anomalies that might indicate a breach. Inventory management features within RMM also aid in regulatory compliance by providing a clear audit trail of all IT assets, their configurations, and security status. This comprehensive approach reduces the attack surface and proactively mitigates potential security risks.
What are the key advantages of leveraging RMM (Remote Monitoring and Management) software for tracking and managing software licenses across multiple client endpoints?
Leveraging RMM software for tracking and managing software licenses across multiple client endpoints offers several key advantages. Firstly, it provides centralized visibility into all installed software and their associated licenses, eliminating the need for manual tracking. This centralized view allows you to easily identify underutilized or expired licenses, optimizing software spending and avoiding costly compliance penalties. RMM tools can automate software deployment and updates, ensuring that all endpoints are running licensed and approved versions. Automated reports can be generated to track license usage, compliance status, and potential cost savings. The ability to remotely manage software licenses also reduces the administrative burden on IT staff, freeing up their time for more strategic initiatives. By proactively managing software licenses through RMM, businesses can maintain compliance, optimize software investments, and improve overall operational efficiency.
Beyond basic inventory, what advanced reporting and automation capabilities should I look for in RMM software to effectively manage my IT assets?
Beyond basic inventory, look for RMM software that provides advanced reporting and automation capabilities to effectively manage your IT assets. Essential features include customizable reporting dashboards that offer real-time insights into asset health, performance, and security status. Automated alerting based on predefined thresholds (e.g., low disk space, high CPU usage, security vulnerabilities) allows for proactive issue resolution. Patch management automation is crucial, enabling you to automatically deploy security updates and software patches across all managed devices. Look for RMM solutions that offer scripting capabilities for automating repetitive tasks such as software installations, configuration changes, and system maintenance. Integration with other IT management tools, such as ticketing systems and documentation platforms, streamlines workflows and improves collaboration. Finally, the ability to generate compliance reports that demonstrate adherence to industry regulations (e.g., HIPAA, GDPR) is essential for maintaining a secure and compliant IT environment. These features ensure efficient and proactive IT asset management.